Dejpaad
Компания по сетевой инженерии и безопасности
Интегрированная защитная реакция вашего бизнеса против кибератак
С почти десятилетним опытом, Dejpaad является одним из пионеров в области сетевой инженерии и безопасности, предоставляющим решения на основе современных информационно-коммуникационных технологий, имея представителей ведущих экспертных брендов в этой области. До сегодняшнего дня Dejpaad обеспечивает безопасность данных бесчисленных крупных и малых предприятий. Позвольте нам снять стресс с вашего дня переезда – чтобы вы могли насладиться им!
-
Организации, предприятия и малые бизнесы всегда обеспокоены защитой своих ценных данных, и только обеспечив безопасность данных и сети, они смогут прочно ступить на следующую ступень развития. Dejpaad – это надежный партнер для развития вашей организации, гарантирующий безопасность и защиту ваших данных.
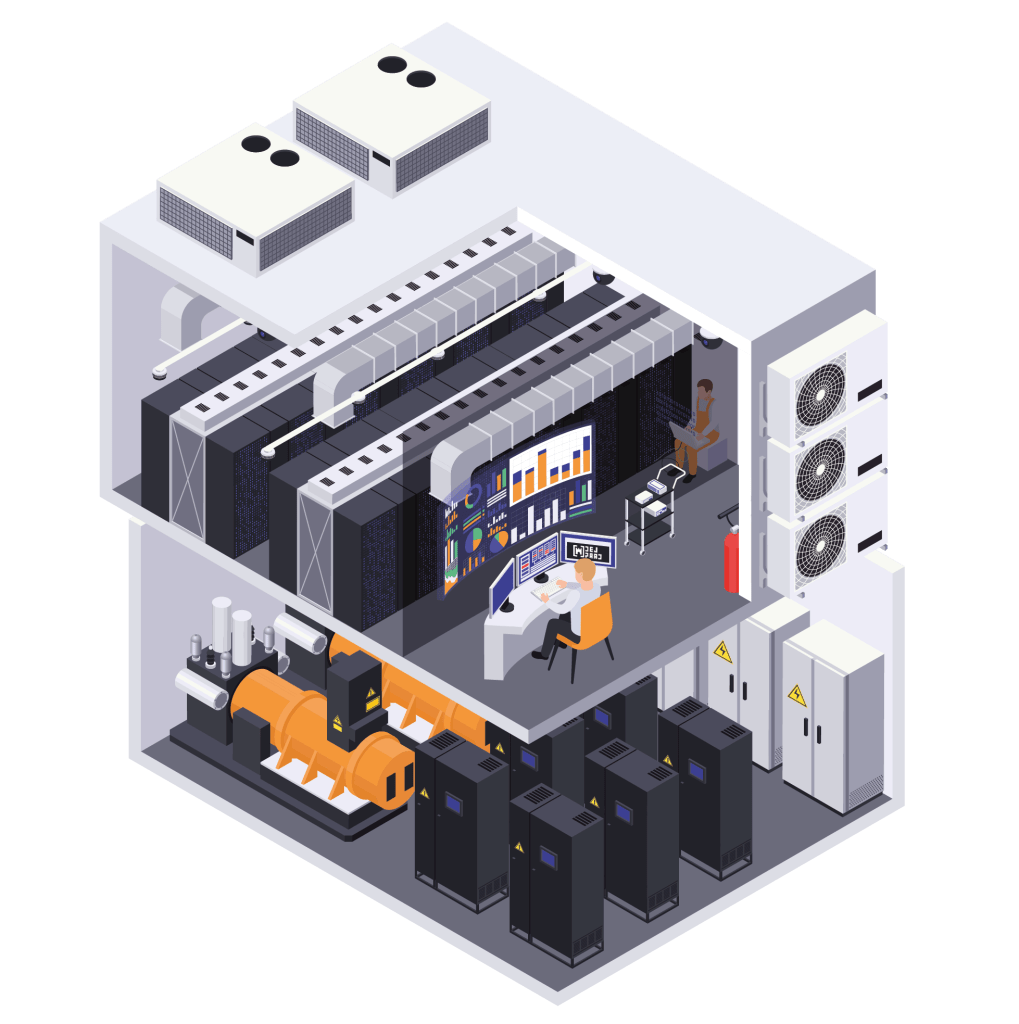
Компания Dejpaad
[Поставщик сетевого оборудования]
Вычисления
Компания Dejpaad предлагает передовые решения в области вычислительных технологий, обеспечивая клиентам высокую производительность и эффективность вычислений для разнообразных бизнес-задач.
Хранение
Наши продукты для хранения данных обеспечивают надежность и масштабируемость, предоставляя клиентам инновационные решения для эффективного управления и хранения ценной информации.
Сетевая инфраструктура
Dejpaad предлагает современные решения для построения надежной и масштабируемой сетевой инфраструктуры, обеспечивая клиентам стабильное и высокопроизводительное взаимодействие.
Безопасность сети | Аппаратное обеспечение
Наши аппаратные решения по обеспечению безопасности сети гарантируют защиту от угроз и вредоносных атак, обеспечивая надежность и безопасность бизнес-сетей.
Безопасность сети | Программное обеспечение
Dejpaad предлагает программные продукты для обеспечения высокого уровня безопасности сети, обнаружения угроз и эффективного управления безопасностью данных.
Управление | Мониторинг
Наши решения в области управления и мониторинга обеспечивают клиентам централизованный контроль и эффективное управление сетевыми ресурсами, повышая общую производительность и надежность инфраструктуры.
Скачать каталог
Скачайте наш каталог, чтобы исследовать обширный ассортимент продуктов, услуг и решений, созданных для удовлетворения ваших конкретных потребностей. Получите подробное представление о наших предложениях и возможностях.

Услуги облачных вычислений
Услуги сетевой безопасности и инфраструктуры
Вычислительные и хранения данных
SIEM
[Внедрение и поддержка]
Мы гордимся предоставлением комплексных решений, тщательно адаптированных для беспроблемной интеграции в вашу существующую инфраструктуру. Наша выделенная команда экспертов берет на себя полный процесс внедрения, обеспечивая плавный переход и минимальные помехи для ваших операций. С начального планирования до развертывания, мы обязаны обеспечивать тщательное внимание к деталям и полную поддержку. После внедрения наши услуги постоянной поддержки гарантируют, что ваши системы продолжают работать с максимальной эффективностью. Будь то устранение неполадок, обновления или реагирование на изменяющиеся потребности, наша служба поддержки всегда готова предоставить своевременную и надежную помощь, позволяя вам сосредотачиваться на основных бизнес-целях с уверенностью в надежности и производительности вашей технологии.
-
Традиционные архитектуры сетевой инфраструктуры не предназначены для обеспечения безопасности современных корпоративных сетей. Чтобы обеспечить безопасность ваших данных и сетевой инфраструктуры бизнеса, вам необходимы обновленные программные и аппаратные инструменты от ведущих производителей в мире.
[Решения в области сетей и сетевой безопасности]
Наша компания специализируется на предоставлении современных решений в области сетевых технологий и сетевой безопасности. Мы предлагаем высокотехнологичные продукты и услуги, обеспечивающие надежность и эффективность в построении и обеспечении работоспособности сетей. Наш опытный коллектив инженеров и специалистов готов обеспечить поддержку на всех этапах – от проектирования до внедрения и последующего обслуживания. Мы стремимся создавать инновационные решения, которые соответствуют современным требованиям безопасности и обеспечивают непрерывную и стабильную работу вашей сетевой инфраструктуры.

Supply of Equipment
To ensure that organizations have the necessary equipment, the following steps must be taken: identifying equipment needs, selecting a reliable supplier, requesting proposals, evaluating and selecting the best proposal, and making bulk purchases.
Integrated solutions
Our integrated solutions seamlessly bring together cutting-edge technologies, creating a unified and efficient environment for your organization. From network infrastructure to security protocols, we tailor comprehensive solutions to optimize operations and enhance overall performance.
Desktop Virtualization
By centralizing the desktop management, it provides flexibility, security, and efficient resource utilization, allowing users to access their virtual desktops from various devices while maintaining a consistent and controlled computing experience.
Desktop as a Service
In DaaS, the desktop environment is hosted and managed by a third-party cloud service provider, offering organizations a scalable, flexible, and accessible solution without the need for extensive on-premises infrastructure.
Backup
Backup solution offers a robust and reliable method for safeguarding your critical data. With automated and regular backups, it ensures the resilience of your information, providing a secure and efficient way to recover in the face of unexpected data loss or system failures.
Disaster Prevention
Disaster Prevention involves implementing proactive measures to mitigate potential risks and minimize the impact of unforeseen events on your organization’s operations. By identifying vulnerabilities, creating contingency plans, and employing preventive strategies, businesses can enhance their resilience and maintain continuity in the face of disasters.
Disaster Recovery
Disaster Recovery is a strategic approach that focuses on restoring IT systems and data quickly after a disruptive event. By having a well-defined plan in place, organizations can minimize downtime, recover critical functions, and ensure business continuity in the aftermath of a disaster.
SDx
Software-defined everything is an innovative approach that virtualizes and abstracts various infrastructure elements, including storage, networking, and computing, allowing for greater flexibility and automation in managing IT resources. This transformative concept enhances adaptability, scalability, and efficiency across diverse aspects of the IT infrastructure.
SDN
Software-Defined Networking, revolutionizes traditional network management by centralizing control and programmatically managing the network infrastructure through software applications. This approach enhances agility, scalability, and adaptability, empowering organizations to efficiently meet the dynamic demands of modern networking environments.
SDS
Software-Defined Storage is an approach that virtualizes and abstracts storage resources, allowing for centralized management and allocation of storage capacity through software. SDS enhances flexibility, scalability, and cost-effectiveness, enabling organizations to optimize their storage infrastructure to meet changing data storage requirements.
SD-WAN
Software-Defined Wide Area Network, is a technology that leverages software-based controls and automation to optimize the management of wide area networks. It enhances network performance, increases agility, and reduces costs by intelligently routing traffic across multiple connections, including broadband internet, MPLS, and 4G/5G, based on application and network conditions.
SDI
Software-Defined Infrastructure revolutionizes traditional IT by abstracting and virtualizing hardware resources, enabling dynamic and programmable management through software applications. This innovative approach enhances agility, scalability, and adaptability, empowering organizations to optimize their infrastructure and respond efficiently to evolving business needs.
SDC
Software-Defined Compute is a paradigm that virtualizes and abstracts computing resources, allowing for dynamic and automated control through software. By separating the control plane from the underlying hardware, SDC enhances flexibility and scalability, enabling efficient utilization of compute resources in response to changing workload demands.
Network Hardening
Network hardening involves implementing security measures to strengthen the resilience of a network against cyber threats. By securing vulnerabilities, restricting unnecessary access, and applying rigorous security protocols, organizations can enhance the overall security posture of their networks and safeguard against potential breaches.
Security Configuration Management
Security Configuration Management involves the systematic process of establishing and maintaining a secure baseline for an organization’s systems and applications. By continuously monitoring and adjusting security settings, organizations can mitigate potential vulnerabilities, ensuring a robust and resilient security posture across their IT infrastructure.
Microsegmentation
Microsegmentation is a security strategy that involves dividing a network into smaller, isolated segments to enhance control and limit lateral movement for potential attackers. By implementing fine-grained security policies at the individual workload level, organizations can significantly strengthen their overall network security and protect critical assets from unauthorized access or lateral threats.
Zero Trust
Zero Trust is a security model that assumes no implicit trust, even for users or devices inside the network perimeter. It requires continuous verification of identities, strict access controls, and comprehensive monitoring to ensure security across all network components and transactions.
Monitoring
Monitoring involves the continuous observation and analysis of systems, networks, or applications to ensure optimal performance, identify potential issues, and respond promptly to irregularities. By proactively tracking key metrics and events, organizations can maintain the health and security of their IT environment, minimizing downtime and enhancing overall operational efficiency.
Data Center Management
A Data Center Management Strategy is a comprehensive plan that addresses the efficient operation, optimization, and future development of a data center. It encompasses aspects such as resource allocation, energy efficiency, security, and scalability, ensuring that the data center aligns with organizational goals, adapts to evolving technology trends, and maintains high performance and reliability.
Automation
Automation involves deploying technology to perform tasks without manual intervention, streamlining processes, reducing errors, and increasing efficiency. By automating routine and repetitive operations, organizations can enhance productivity, accelerate workflows, and focus human resources on more strategic and complex initiatives.
Supply of Equipment
To ensure that organizations have the necessary equipment, the following steps must be taken: identifying equipment needs, selecting a reliable supplier, requesting proposals, evaluating and selecting the best proposal, and making bulk purchases.
Integrated solutions
Our integrated solutions seamlessly bring together cutting-edge technologies, creating a unified and efficient environment for your organization. From network infrastructure to security protocols, we tailor comprehensive solutions to optimize operations and enhance overall performance.
Desktop Virtualization
By centralizing the desktop management, it provides flexibility, security, and efficient resource utilization, allowing users to access their virtual desktops from various devices while maintaining a consistent and controlled computing experience.
Desktop as a Service
In DaaS, the desktop environment is hosted and managed by a third-party cloud service provider, offering organizations a scalable, flexible, and accessible solution without the need for extensive on-premises infrastructure.
Backup
Backup solution offers a robust and reliable method for safeguarding your critical data. With automated and regular backups, it ensures the resilience of your information, providing a secure and efficient way to recover in the face of unexpected data loss or system failures.
Disaster Prevention
Disaster Prevention involves implementing proactive measures to mitigate potential risks and minimize the impact of unforeseen events on your organization’s operations. By identifying vulnerabilities, creating contingency plans, and employing preventive strategies, businesses can enhance their resilience and maintain continuity in the face of disasters.
Disaster Recovery
Disaster Recovery is a strategic approach that focuses on restoring IT systems and data quickly after a disruptive event. By having a well-defined plan in place, organizations can minimize downtime, recover critical functions, and ensure business continuity in the aftermath of a disaster.
SDx
Software-defined everything is an innovative approach that virtualizes and abstracts various infrastructure elements, including storage, networking, and computing, allowing for greater flexibility and automation in managing IT resources. This transformative concept enhances adaptability, scalability, and efficiency across diverse aspects of the IT infrastructure.
SDN
Software-Defined Networking, revolutionizes traditional network management by centralizing control and programmatically managing the network infrastructure through software applications. This approach enhances agility, scalability, and adaptability, empowering organizations to efficiently meet the dynamic demands of modern networking environments.
SDS
Software-Defined Storage is an approach that virtualizes and abstracts storage resources, allowing for centralized management and allocation of storage capacity through software. SDS enhances flexibility, scalability, and cost-effectiveness, enabling organizations to optimize their storage infrastructure to meet changing data storage requirements.
SD-WAN
Software-Defined Wide Area Network, is a technology that leverages software-based controls and automation to optimize the management of wide area networks. It enhances network performance, increases agility, and reduces costs by intelligently routing traffic across multiple connections, including broadband internet, MPLS, and 4G/5G, based on application and network conditions.
SDI
Software-Defined Infrastructure revolutionizes traditional IT by abstracting and virtualizing hardware resources, enabling dynamic and programmable management through software applications. This innovative approach enhances agility, scalability, and adaptability, empowering organizations to optimize their infrastructure and respond efficiently to evolving business needs.
SDC
Software-Defined Compute is a paradigm that virtualizes and abstracts computing resources, allowing for dynamic and automated control through software. By separating the control plane from the underlying hardware, SDC enhances flexibility and scalability, enabling efficient utilization of compute resources in response to changing workload demands.
Network Hardening
Network hardening involves implementing security measures to strengthen the resilience of a network against cyber threats. By securing vulnerabilities, restricting unnecessary access, and applying rigorous security protocols, organizations can enhance the overall security posture of their networks and safeguard against potential breaches.
Security Configuration Management
Security Configuration Management involves the systematic process of establishing and maintaining a secure baseline for an organization’s systems and applications. By continuously monitoring and adjusting security settings, organizations can mitigate potential vulnerabilities, ensuring a robust and resilient security posture across their IT infrastructure.
Microsegmentation
Microsegmentation is a security strategy that involves dividing a network into smaller, isolated segments to enhance control and limit lateral movement for potential attackers. By implementing fine-grained security policies at the individual workload level, organizations can significantly strengthen their overall network security and protect critical assets from unauthorized access or lateral threats.
Zero Trust
Zero Trust is a security model that assumes no implicit trust, even for users or devices inside the network perimeter. It requires continuous verification of identities, strict access controls, and comprehensive monitoring to ensure security across all network components and transactions.
Monitoring
Monitoring involves the continuous observation and analysis of systems, networks, or applications to ensure optimal performance, identify potential issues, and respond promptly to irregularities. By proactively tracking key metrics and events, organizations can maintain the health and security of their IT environment, minimizing downtime and enhancing overall operational efficiency.
Data Center Management
A Data Center Management Strategy is a comprehensive plan that addresses the efficient operation, optimization, and future development of a data center. It encompasses aspects such as resource allocation, energy efficiency, security, and scalability, ensuring that the data center aligns with organizational goals, adapts to evolving technology trends, and maintains high performance and reliability.
Automation
Automation involves deploying technology to perform tasks without manual intervention, streamlining processes, reducing errors, and increasing efficiency. By automating routine and repetitive operations, organizations can enhance productivity, accelerate workflows, and focus human resources on more strategic and complex initiatives.
Независимо от сферы, в которой работает ваш бизнес, обеспечение безопасности данных вашей организации – наша специализация.
[Схема сотрудничества и реализации проектов в Dejpaad]
Наша команда состоит из опытных экспертов в области сетевой безопасности, которые предлагают лучшие решения в области безопасности, проанализировав требования и сетевую инфраструктуру организации. Некоторые из наших услуг включают консультирование, внедрение и мониторинг сетевой безопасности, обучение и информирование сотрудников, тестирование на проникновение и управление рисками. Наша цель – предоставить решения, защищающие организации от угроз безопасности и повышающие уровень сетевой безопасности
3
Проведение личных встреч и представление экспертного предложения
2
Консультирование и краткое введение в оборудование и предоставление экспертных решений
1
Общение с отделом продаж
6
Планирование и представление “Плана реализации проекта” в проектах по установке и внедрению
5
Заключение контракта и назначение исполнительных обязанностей и обязательств
4
Предоставление настройки продукта и решений командой экспертов по продукту
9
Определение ролей и ответственностей на основе матрицы RACI
8
Планирование и предоставление планов поддержки/гарантии в сервисно-ориентированных проектах
7
Регистрация заказа и представление плана закупки и доставки оборудования в товарно-ориентированных проектах
12
Развитие и поддержание организационных отношений с клиентами
11
Завершение и передача проекта
10
Контроль проекта